- Jan 5, 2026
Exploring Digital Identity Guidelines by NIST
- Daniel Krzyczkowski
In an increasingly interconnected world, verifying who we are online and ensuring that identity information stays secure and private has become one of the foundational challenges of information security. To meet this challenge, the National Institute of Standards and Technology (NIST) has developed a set of comprehensive standards known as the Digital Identity Guidelines. These are formalized in NIST Special Publication (SP) 800-63, currently in its fourth revision (v 4.0), and are widely recognized as authoritative guidance for identity proofing, authentication, and federated identity systems.
The NIST Digital Identity Guidelines are a suite of documents that provide technical and procedural requirements for establishing and managing digital identity services. Their main goal is to help organizations, particularly U.S. federal agencies, implement identity systems that are secure, privacy-protective, usable, and risk-based. These guidelines are not laws, but they influence regulatory frameworks and best practices globally. They inform how real-world identities can be reliably tied to digital identities for transactions ranging from logging into online services to accessing sensitive systems.
What Is NIST SP 800-63-4
NIST SP 800-63 is a suite of publications that together define how digital identity should be established, authenticated, and shared securely. SP 800-63 is organized as the following suite of volumes:
SP 800-63 (Digital Identity Guidelines) serves as the foundation of the suite. It defines digital identity models, introduces a risk-based approach to identity decisions, and explains how organizations select appropriate assurance levels for identity proofing, authentication, and federation.
SP 800-63A (Identity Proofing and Enrollment) focuses on how individuals are verified and enrolled, either remotely or in person. It outlines requirements for identity proofing at each Identity Assurance Level (IAL) and describes the responsibilities of Credential Service Providers (CSPs) in creating and managing subscriber accounts and binding authenticators to those accounts.
SP 800-63B (Authentication and Lifecycle Management) defines requirements for authentication at each Authenticator Assurance Level (AAL). It covers acceptable authenticator types and provides guidance on managing authenticators throughout their lifecycle, including replacement and revocation in cases such as loss or compromise.
SP 800-63C (Federation and Assertions) addresses federated identity systems, specifying how authentication results and identity information can be securely shared between organizations using federated architectures and assertions.
Together, these documents provide a comprehensive, risk-based framework for building secure, interoperable, and trustworthy digital identity systems.
A digital identity represents a person online, whether it’s for accessing a banking app, logging into a government service, or registering for an educational portal. But identity is tricky:
Digital accounts may not reflect the person’s real-world identity
Online systems face persistent threats such as fraud, impersonation, and automated attacks
Users expect fast, friction-free experiences without sacrificing safety
SP 800-63-4 helps organizations manage these trade-offs by putting security, privacy, and usability on equal footing and by encouraging risk-based decisions, not rigid checklists.
Assurance Levels: The Heart of the Framework
Instead of a single, one-size-fits-all trust level, SP 800-63-4 uses three modular assurance dimensions - each describing how confident an organization should be at different stages of the identity lifecycle.
Identity Assurance Level (IAL)
NIST defines three levels of identity evidence based on how reliable and verifiable they are:
Fair Evidence: Issued after some identity check (e.g., bank account setup, mobile phone account). Contains personal identifiers, some security features, and core attributes. Can be validated and support verification.
Strong Evidence: Issued using more rigorous, written identity proofing procedures (e.g., government‑regulated documents). Includes biometric or photo, secure features, and can be thoroughly validated.
Superior Evidence: Highest confidence: strong issuance process, cryptographically protected, and usually issued after in‑person proofing. Supports strong verification methods.
Assurance (confidence) in a subscriber’s identity is established using the processes associated with the identity assurance levels (IAL) defined in the NIST guidelines. Each successive IAL builds on the requirements of lower IALs in order to achieve increased assurance. Identity Assurance Level (IAL) measures confidence that a claimed identity actually belongs to a specific person. It covers how strongly an identity is proofed before being accepted.
There are typically three levels:
IAL1: Minimal proofing: e.g., self-asserted identity without verification
IAL2: Verified identity: uses trustworthy evidence (e.g., government ID, remote verification)
IAL3: Highest confidence: rigorous proofing with strong identity evidence and verification processes
Higher IALs reduce the risk of impersonation and fraud. The below table (from NIST documentation) summarizes the requirements for each of the identity assurance levels:
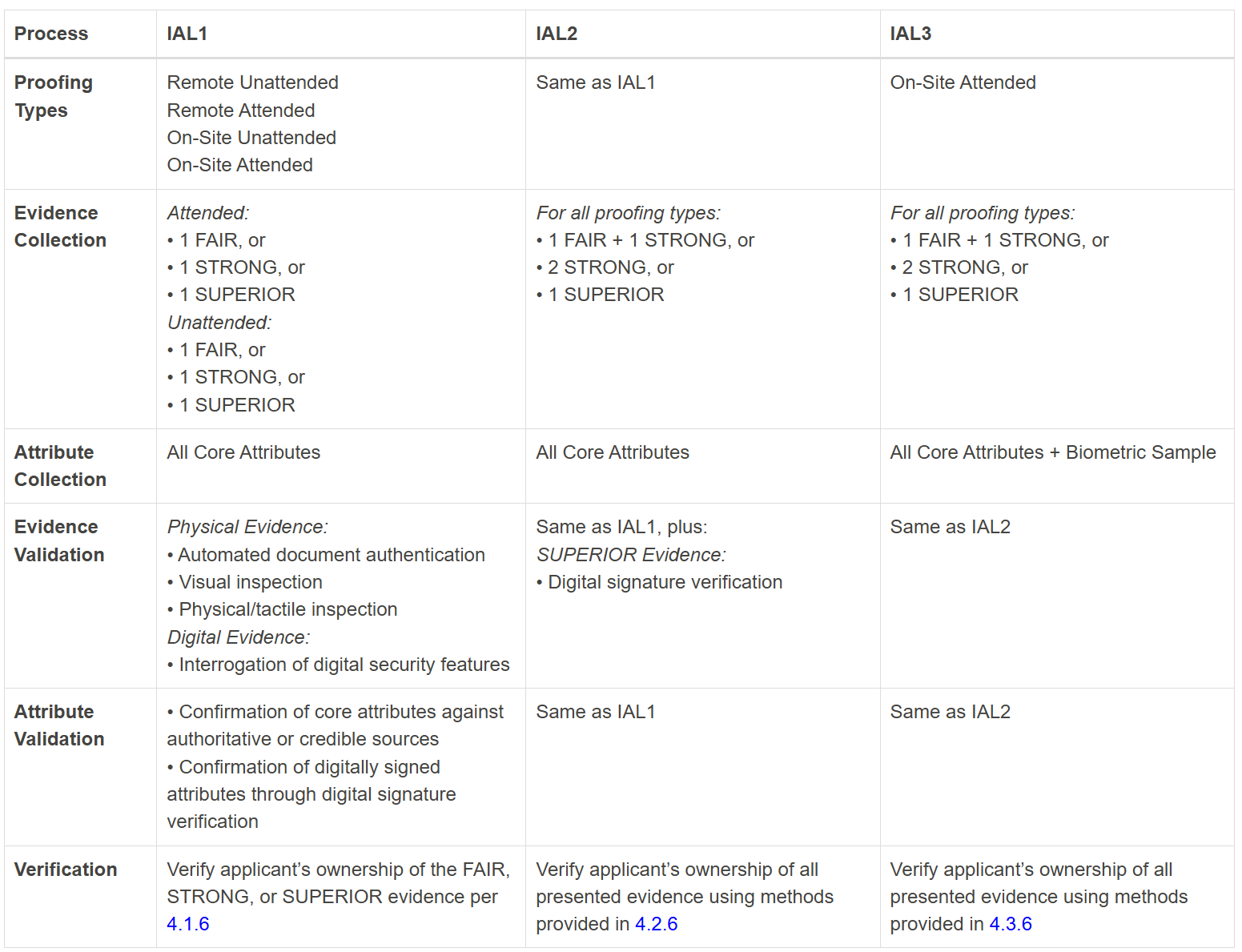
Authenticator Assurance Level (AAL)
Authenticator Assurance Level (AAL) determines how strong the login process is. It describes how identity is authenticated, not just what credentials are used, but how resistant the process is to attack. Three levels are defined:
AAL1: Basic authentication (e.g., single factor, like username and password)
AAL2: Multi-factor authentication (e.g., username/password + SMS OTP)
AAL3: High-security authentication (e.g., hardware cryptographic tokens, like FIDO2 security keys)
At higher AALs, passwords alone are usually insufficient; stronger methods (like phishing-resistant authenticators) are required. Here is the summary from NIST official documentation:
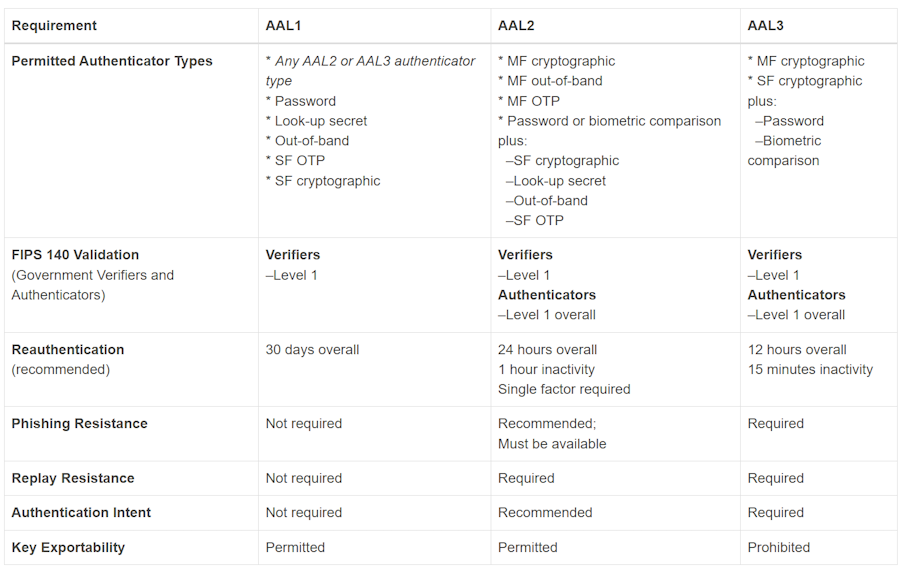
Federation Assurance Level (FAL)
Federation Assurance Levels (FAL) define how securely identity information is shared between systems when federated identity is used. Federation comes into play when an Identity Provider (also called IdP) authenticates a user and then passes the authentication result along with identity attributes to an application (also called Relying Party, or RP). Common examples include:
Sign in with a government ID
Enterprise single sign-on (SSO)
Customer authentication to e-commerce app
FAL focuses not on how the user authenticates, but on how authentication results and identity data are protected and trusted as they move between systems (like between Identity Provider and Application).
Like IAL and AAL, FAL has three tiers:
FAL1: Basic federated assertions (e.g., signed tokens)
FAL2: Stronger, cryptographically protected assertions (e.g., signed and encrypted tokens)
FAL3: Highest security federation with additional safeguards (e.g., tokens are signed, encrypted, and cryptographically bound to a holder which means that bearer tokens are not allowed)
The below table presents federation assurance levels and requirements:
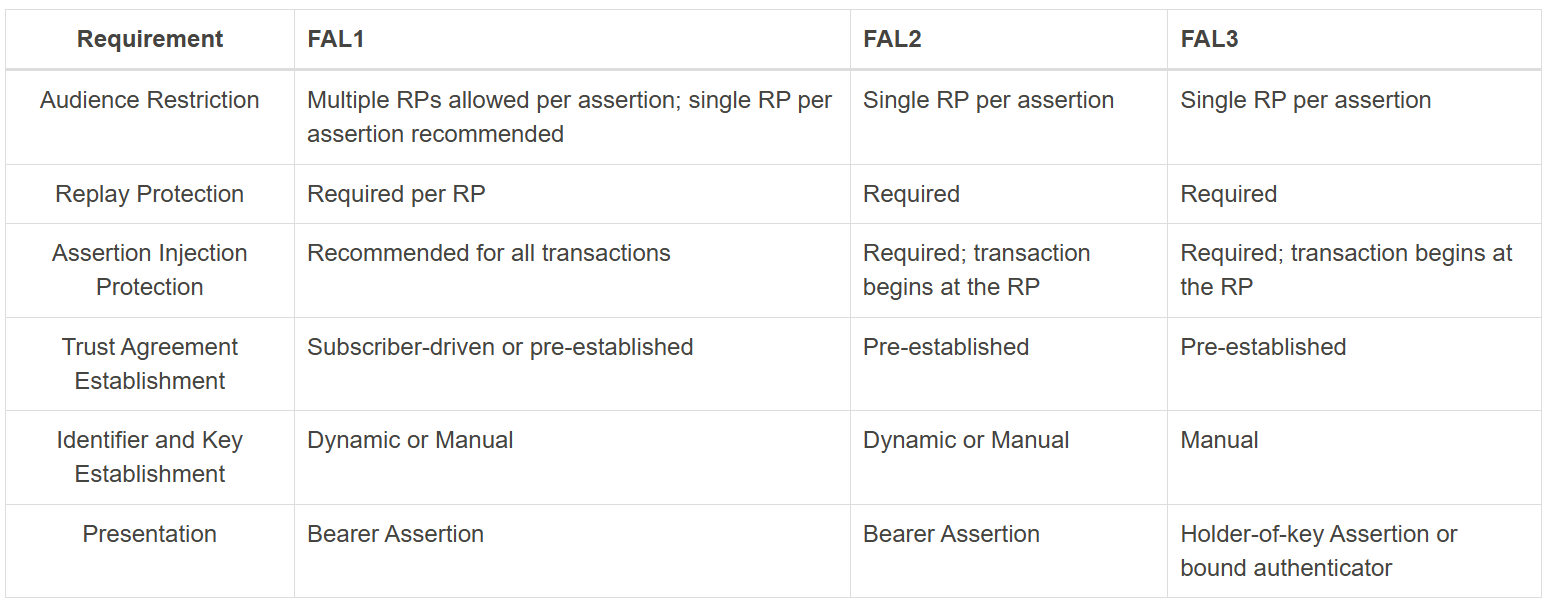
Understanding DIRM (Digital Identity Risk Management)
One major innovation in SP 800-63-4 is a structured focus on Digital Identity Risk Management (DIRM), not just technical controls.
Rather than enforcing a single “compliance” checkbox, the guidelines encourage organizations to:
Understand the risks associated with identity proofing, authentication, and federation
Measure the potential impact of identity errors
Select appropriate assurance levels for their risk context
Tailor controls and mitigations to organizational needs
In other words, instead of simply complying with rules, organizations must think like defenders, considering threats, business impacts, privacy harms, and user experience. This risk-based mindset makes identity systems stronger and more adaptive. DIRM turns digital identity into a cross-disciplinary exercise involving cybersecurity, business risk, privacy, legal, and user experience stakeholders. Organizations are encouraged not just to meet minimum standards, but to continuously evaluate and improve identity assurance.
Summary
NIST SP 800-63-4 is not a check-the-box document. It provides:
A modular assurance framework (IAL, AAL, FAL)
A risk management model (DIRM) to guide decisions
Clear definitions of identity functions and roles
Expectations for privacy, usability, and security
This makes it practical for both government and commercial systems - from low-risk user portals to high-security financial or health applications.
Identity isn’t just a username and password anymore. It’s the foundation of trust online. By guiding organizations to:
define how identities are proven,
decide how strongly users should authenticate,
and ensure secure federation,
all while managing risk smartly,
NIST SP 800-63-4 helps make digital systems safer, more private, and more user-friendly. If you would like to read more, visit official NIST SP 800-63-4: Digital Identity Guidelines page.